In April 2016, Let’s Encrypt went live. Let’s Encrypt is a group making it significantly easier to encrypt web traffic. Some entity seems to have begun waging a war of public opinion against them.

Previous to their existence conveniently securing web traffic meant paying money to a company which would then provide you with a “certificate” for your website. Servers and browsers use these certificates to create a secure communication path between them. This secure path (denoted by URLs starting with “https://” rather than “http://”) prevents entities between your computer and the website from seeing or altering the data being sent to and from the website.
Because of the cost and inconvenience many websites used unsecured connections. However, places like banks, shopping, and healthcare providers have pretty much always used secure connections. It took a few years but eventually social media websites began using secure connections by default as well.
Before Let’s Encrypt, millions of websites only had their content available via unsecured communications. For many people, like myself, running websites without any goal of making money from them the expense and hassle of certificates wasn’t worth it. Now, my websites are all available through secured connections, for free, thanks to Let’s Encrypt. (To be clear, many websites still haven’t taken advantage of this service yet, but they at least have the option now.)
But, if banks and such use secure connections anyway, why do we care about Let’s Encrypt, should I care if “someone” can see that I’m reading this blog post?
Maybe.
On March 28 Congress voted to repeal FCC regulations that prevented your Internet Service Provider (ISP) from spying on your web traffic and using that information to their financial benefit. The regulations also prevented ISPs from altering your web traffic for similar purposes (e.g., injecting ads into a webpage when you view it).
Maybe you don’t care if Comcast, or AT&T, or Verizon knows you like to knit and shop at JoAnn’s Fabrics. But maybe you’d be concerned if they started selling information to other companies about you visiting cancer treatment websites, or rape support groups, or divorce attorneys, or any number of kinds of sensitive information.
Using encrypted connections doesn’t solve this problem entirely, but it makes the information available to your ISP a lot less useful. For example, your ISP would still be able to tell you’re looking at Amazon.com, but they wouldn’t be able to tell if you’re looking at knitting needles or books about infertility treatments.
Regardless of your stance, someone seems to be working hard to turn public opinion against Let’s Encrypt and again make it harder to encrypt web traffic. Articles like this one: “14,766 Let’s Encrypt SSL Certificates Issued to PayPal Phishing Sites” have been showing up all over the Internet recently, all making similar claims that it is Let’s Encrypt’s fault that people are falling for fake PayPal scam websites.
I don’t think it’s actually PayPal behind these articles, because this problem is nothing new, but the concerted, direct attack on Let’s Encrypt is new.
Let’s Encrypt does not verify the identity of the person requesting a certificate (which other certificate providers will do for steep fees, $300+ per year, these “verified” certificates are significantly different than the “non-verified” certificates issued by Let’s Encrypt). Instead Let’s Encrypt verifies that you control the website for which you’re requesting a certificate, slightly different.
The argument made by these articles is that now someone can get _a_ certificate for “paypall.com” and people will think that the green lock icon on their browser means they’re connected to “paypal.com” instead. Which it doesn’t and never has. The “verified” certificates show up differently in your browser. For example, on this blog you’ll see something like this:
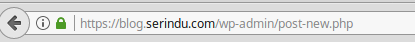
With a “verified” certificate you’ll instead see something like this:
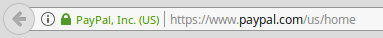
This indicates that the company issuing the certificate verified that the company requesting the certificate is “PayPal, Inc.” and the certificate is for “paypal.com”.
The articles want you believe Let’s Encrypt is somehow at fault if people end up at “paypall.com” with a green lock and think it’s “paypal.com”. Let’s Encrypt isn’t providing “verified” certificates or trying to solve that problem. The problem they’re trying to solve is that too much web traffic is unencrypted by default because certificates were expensive and inconvenient.
Someone with a vested interest in being able to read and/or modify your web traffic has been working really hard to get these articles out and make it look like some kind of “public safety” issue.
I have no idea who that entity may be, but it’s making me really annoyed. Let’s Encrypt is a good thing for anyone that thinks that their Internet communications should be private by default.
Update 3/31: Engadget just ran one of the attack pieces too: “When the ‘S’ in HTTPS also stands for shady“. Which is the most mainstream source running these articles that I’ve seen thus far.
To be completely clear, when a URL starts with HTTPS it only means that your connection is encrypted between your computer and the website–it has never meant anything about who is running the website is or whether the website operator is trustworthy.










































